Search by the «fraud» tag
Trust Escrow tracks the shipped merchandise and verifies it was delivered. The Seller isn’t paid until the Buyer accepts the merchandise, or the inspection period expires. We also confirm when the Buyer receives merchandise. The Seller is authorized to ship only after verifies good fundsMore
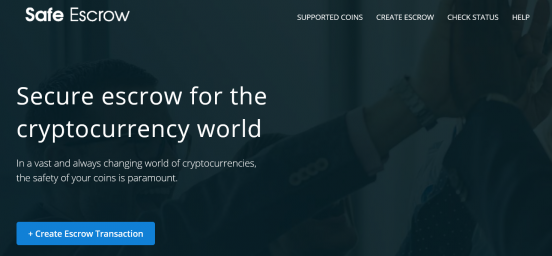
Secure escrow for the cryptocurrency world In a vast and always changing world of cryptocurrencies, the safety of your coins is paramount.More
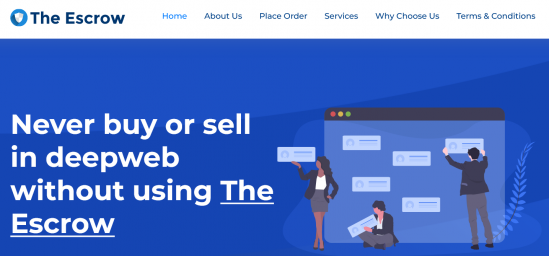
Serving customers since 2015, The Escrow is Your 24x7 Partner for deep web purchases. Your financial security is our No. 1 Priority and hence, we work 24x7 on it to ensure you have secure hassle-free transactions.More
Safely and easily purchase goods or services from unknown or untrusted sellers with bitcoin currency.More
Safely and easily purchase goods or services from unknown or untrusted sellers and stores with bitcoin currency.More
As a vulnerability reporter public issues private issues (embargo) As a package maintainer DSA vulnerability SPU vulnerability Just unstableMore
Three years ago, I wrote about a way to purge only changed static files when deploying a static site. It is very useful and I still use it for this website to this day. Its main advantage is that it only needs to be run on deploys. However, its main disadvantage is that it must be run on every deployment.More
I am a security engineer, a writer, and contributor to the Monero project, a cryptocurrency focused on preserving privacy for transactions data. My publication Mastering Monero has became one of the best rated resources to learn about Monero.More
Choose Better tells you whether a .onion site is scam or not Are you about to buy something from an .onion site and don't want to get scammed? If so, we could help you. We have already tested a lot of sites and we know which are scams and which are not.More
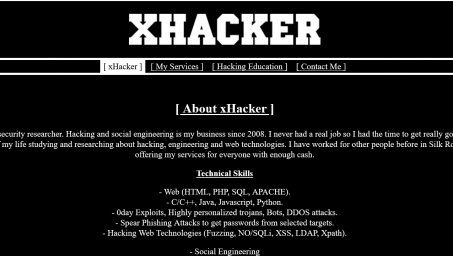
Hire a Hacker, Security Researcher, Offensive Security Web Expert (OSWE), Penetration Tester, Social Engineer. -- Hacking web servers, computers and smartphones. Social Media hacking. Change grades in schools and universities. Information gathering. Exploits, Trojans, RATs, Keyloggers. SQL injections, DoS attacks, Phishing attacks.More
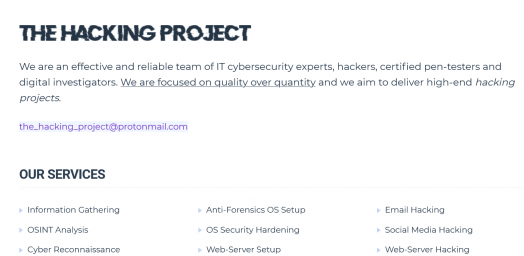
We are an effective and reliable team of IT cybersecurity experts, hackers, certified pen-testers and digital investigators. We are focused on quality over quantity and we aim to deliver high-end hacking projects.More
Hire a hacker for espionage, ruining people, DDOS, hacking, exploits, email or facebook password hack and more. Hacking, Hack, Computer, Spying, Surveillance, Keylogger,DDoS, Tracking,Fraud, Spyware, botnet, Cyber, Extortion, Remove, Hacker, ruining, hackingMore

![[ h4ck3r ] Hacking Services [ h4ck3r ] Hacking Services](../../upload/000/u1/e/4/h4ck3r-hacking-services-photo-normal.png)